Imagine if hackers could use the very system that helps you browse the internet to secretly steal data or take control of a device. Indeed, that’s exactly what happens in a DNS tunneling attack. This means it’s a sneaky method where hackers hide their actions by blending in with regular internet traffic. Nonetheless, don’t worry—understanding how it works will help you protect yourself!
What is DNS Tunneling?
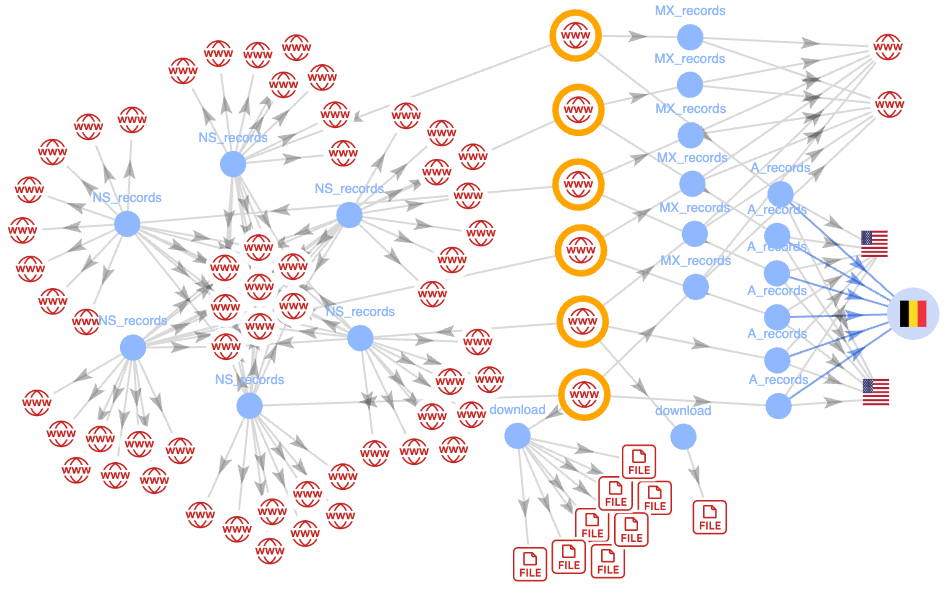
DNS (Domain Name System) is like the phonebook of the internet. Furthermore, it translates website names into numbers (IP addresses) that computers use to talk to each other. Moreover, in a DNS tunneling attack, hackers take advantage of this system to send or receive hidden data.
Why is it dangerous? First and foremost, DNS traffic (which uses port 53) often slips past firewalls without being checked. Thus, hackers exploit this vulnerability to sneak in or out of networks unnoticed.
How Hackers Use DNS Tunneling:
- Step 1 – Infection: Hackers first get malware onto a device—this could be through a phishing email, an infected website, or other tricks.
- Step 2 – Hiding Data: Once they’ve taken over, they break the stolen data into pieces and hide it in what looks like a normal DNS request (e.g.,
stolen-data.attacker-domain[.]com).
- Step 3 – Sending It Out: This hidden data is then sent out, passing through firewalls as if it were regular web traffic, without setting off any alarms.
- Step 4 – Command and Control: Hackers can also use DNS to send commands back to the infected device, keeping control over it.
Real-Life Attacks Using DNS Tunneling
Here are some real-world examples of how cybercriminals have used DNS tunneling to cause serious damage:
FinHealthXDS Campaign: Hackers targeted the finance and healthcare industries, using DNS tunneling to control infected computers. They even used specific IP addresses, like
40.112.72[.]205, and special code in their DNS requests to fly under the radar.
RussianSite Campaign: This attack involved more than 100 different websites, mostly using
.siteand.websitedomains, to steal data from across the globe. It’s linked to an IP address from Russia:185.161.248[.]253.
8NS Campaign: In this case, hackers used six different websites with the same setup, all pointing to the IP address
35.205.61[.]67. These sites worked together to move data out of networks without being detected.
NSfinder Campaign: This attack tricked people through adult websites, stealing credit card information with malware like IcedID and RedLine Stealer. The hackers used IP addresses such as
185.176.220[.]80and185.176.220[.]212to pull off the attack.
How to Spot DNS Tunneling
To protect yourself, watch for these signs:
Strange Website Names: Hackers often use weird or suspicious domain names. Some examples of malicious ones include:
codeaddon[.]netlifemedicalplus[.]netlustypartnersfinder[.]com
Suspicious IP Addresses: Certain IP addresses have been linked to DNS tunneling attacks, such as:
88.119.169[.]205185.161.248[.]253185.176.220[.]80
Malicious Files: If your system is infected, it might have files like these:
0b99db286f3708fedf7e2bb8f24df1af13811fe46b017b6c3e7e002852479430dfb3e5f557a17c8cdebdb5b371cf38c5a7ab491b2aeaad6b4e76459a05b44f28
Conclusion
Ultimately, DNS tunneling is a crafty way hackers hide their tracks and steal data without being noticed. Thus, by keeping an eye on unusual domains, strange IP addresses, and suspicious activity, you can help protect your network from these hidden threats. In summary, stay alert and make sure your security systems are ready for anything!
Disclaimer: The content provided in this article is for educational purposes only. HackTheNix does not endorse or promote any illegal activities. Readers are encouraged to use the information responsibly and within the boundaries of the law.(alert-warning)
.jpeg)



.png)
